Why IT Shouldn't Complete Your Cyber Insurance Application

"My client's MSP completes their cyber insurance application for them. They know more about the company's security practices than the client.", said "Bob" the insurance broker. The business and technology attorney, "Stan", and I had a similar, alarmed reaction. This lunch comment led the three of us to the all-too-familiar topic:
What is an MSP?
What do they do?
Why does it matter?
It's common in the technology space to hear people toss around terms and labels for who does what. The problem is, unless you have firsthand knowledge, the words are often misapplied and misunderstood. MSP is a perfect example of this.
Describing an MSP is like the parable of the elephant and the six blind men. These men had never seen an elephant and were eager to discover what one looked like. At last, the day came when these six curious men encountered their first elephant. Each touched a part of the elephant. Based on their uninformed experience and limited knowledge, each man decided he knew what an elephant looked like.
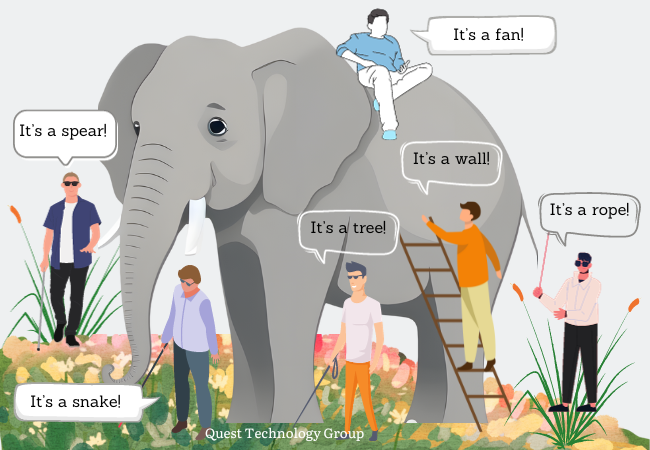
And that's how an MSP becomes the elephant in the room.
MSP is short for Managed Service Provider. These folks have been outsourced technology providers since the early days of business meets technology. As technology has evolved and become more complex, MSPs' skills, sophistication, and expertise have remained largely stagnant.
This is important. There's a huge disconnect between the services that an MSP provides and the essential expertise that a company leader believes they're receiving. MSPs imply through omission – and company leaders assume – that they take care of all your technology needs. This simply isn't possible.
Technology's complexity requires a foundation of business-first thinking for even the smallest company.
In our experience, MSPs primarly focus on:
Applying Windows updates and patches to on-premises servers, desktops, and laptops
Some many extend this support to cloud infrastructure providers such as Azure and AWS
Supporting on-premises, company-owned devices including servers, desktops, laptops, printers, routers, and switches
Third-party backup solution of some kind
Microsoft-provided virus protection
Some many offer more comprehensive proactive security monitoring through third-party providers
These are just some of the core technology areas that need continuous oversight in every company:
Support employee-owned devices used for company business
Support mobile devices
Recommend, help create, and enforce company-wide technology policies and procedures
Provide systematic, proactive employee onboarding, midboarding, and offboarding support
Unless they have hired experienced, certified cybersecurity specialists, they do not provide the essential cybersecurity protection companies expect
Support for the software and applications you rely on for day-to-day operations
Valuable data protection that we know third-party providers don't provide either
Monitoring for unauthorized or potentially risky applications
One additional thought--
While MSPs are third-party providers, your internal IT team often has many of the same skillsets. So whether outsourcing to an MSP or relying on your internal IT folks, you need to have a clear understanding of what they bring to your overall technology foundation.
Coming back to our lunchtime conversation, never ask an internal or outsourced IT team member to complete a cyber insurance – or any form of insurance coverage– application for you.
Why?
Their knowledge of your business and security practices only extends to what they know they have done at a single point in time.
They don't know how third-party application providers safeguard your company data
They don't even know where all of your data lives
They don't have control over how third-party applications enforce MFA
They don't have control over what employees are doing on their personal devices for company business
They don't have control over applications that users are downloading or accessing online unless your company has a strict, enforceable shadow IT policy
They don't know who has been granted access to your network, and your risk exposure
The list goes on, but you get the point.
A conscientious IT provider wants to please you. This means doing what you ask even when they might be uncomfortable or unqualified to do so.
Your business and technology needs are continually changing. Decisions aren't one and done. Scheduling regular conversations with all of your IT team -- both internal and outsourced -- is a smart, tech-savvy leadership practice.
We know the thought of a business-centered conversation with technology people can feel painful. This ebook will help you start the discussion. It includes some questions to ask and plain English answers to listen for. We've also included a handy matrix of who does what on today's IT teams.
It's common in the technology space to hear people toss around terms and labels for who does what. The problem is, unless you have firsthand knowledge, the words are often misapplied and misunderstood. MSP is a perfect example of this.
The Perfect Parable
Describing an MSP is like the parable of the elephant and the six blind men. These men had never seen an elephant and were eager to discover what one looked like. At last, the day came when these six curious men encountered their first elephant. Each touched a part of the elephant. Based on their uninformed experience and limited knowledge, each man decided he knew what an elephant looked like.

And that's how an MSP becomes the elephant in the room.
What is an MSP?
MSP is short for Managed Service Provider. These folks have been outsourced technology providers since the early days of business meets technology. As technology has evolved and become more complex, MSPs' skills, sophistication, and expertise have remained largely stagnant.
Why Does This Matter?
This is important. There's a huge disconnect between the services that an MSP provides and the essential expertise that a company leader believes they're receiving. MSPs imply through omission – and company leaders assume – that they take care of all your technology needs. This simply isn't possible.
Technology's complexity requires a foundation of business-first thinking for even the smallest company.
What Services Do MSPs Provide?
In our experience, MSPs primarly focus on:
What Don't MSPs Do?
These are just some of the core technology areas that need continuous oversight in every company:
One additional thought--
While MSPs are third-party providers, your internal IT team often has many of the same skillsets. So whether outsourcing to an MSP or relying on your internal IT folks, you need to have a clear understanding of what they bring to your overall technology foundation.
What You Should Never Ask IT To Do For You
Coming back to our lunchtime conversation, never ask an internal or outsourced IT team member to complete a cyber insurance – or any form of insurance coverage– application for you.
Why?
Their knowledge of your business and security practices only extends to what they know they have done at a single point in time.
The list goes on, but you get the point.
A conscientious IT provider wants to please you. This means doing what you ask even when they might be uncomfortable or unqualified to do so.
Your Easy Action Item
Your business and technology needs are continually changing. Decisions aren't one and done. Scheduling regular conversations with all of your IT team -- both internal and outsourced -- is a smart, tech-savvy leadership practice.
We know the thought of a business-centered conversation with technology people can feel painful. This ebook will help you start the discussion. It includes some questions to ask and plain English answers to listen for. We've also included a handy matrix of who does what on today's IT teams.
Thanks for Stopping By on Wednesday
Discover what other successful company leaders know.
Join our community of tech savvy business leaders. We share information, knowledge, tools, resources, and a connected community to help you and your business thrive.
 Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable, lasting client relationships.
Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable, lasting client relationships. She loves discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner.
Tags: Technology Strategy
