What is the Difference Between Cybersecurity Risk Tolerance and Risk Appetite

I was having coffee with a fellow CIO, and she shared one of the all too familiar managed service provider experiences. She interviewed MSPs to complement her organization’s internal IT team. One of these potential providers said her company would need to replace all of their HP network equipment with Cisco because that was the skillset the MSP had.
Obviously, this MSP wasn’t invited to join her team. Making a change of this scope was a significant financial investment with zero benefit to the organization. Technology drives the business is an all-too-common stance that IT providers take and it’s simply wrong.
Technology's job is to serve your business. Period.
That brings us to the topic we all dread hearing about – security. Stay with me for a minute. This is actually fun and useful -- not fearmongering.
We each have our own attitude about security for both our business and personal peace of mind. We’ve had company leaders tell us they’re not concerned about security:
While some of these excuses might have made sense a few years ago, they don’t hold up in the face of today’s sophisticated security hackers.
Let’s assume that you're a practical, informed leader. You know that an unexpected security event can happen at some point. How do you sift through the hype, promises, baffling words, and uncertainty with confidence?
As we know from our misguided MSP example, responsible security protection -- like all technology -- isn’t a one-size-fits-all solution. Do what my CIO friend did. Keep looking for the provider who understands your specific business needs before selling the quick and easy solution.
If an IT provider tells you that they have everything you need before asking you these three questions, don’t fall for it.
Start By Clarifying Your Own Risk Realities
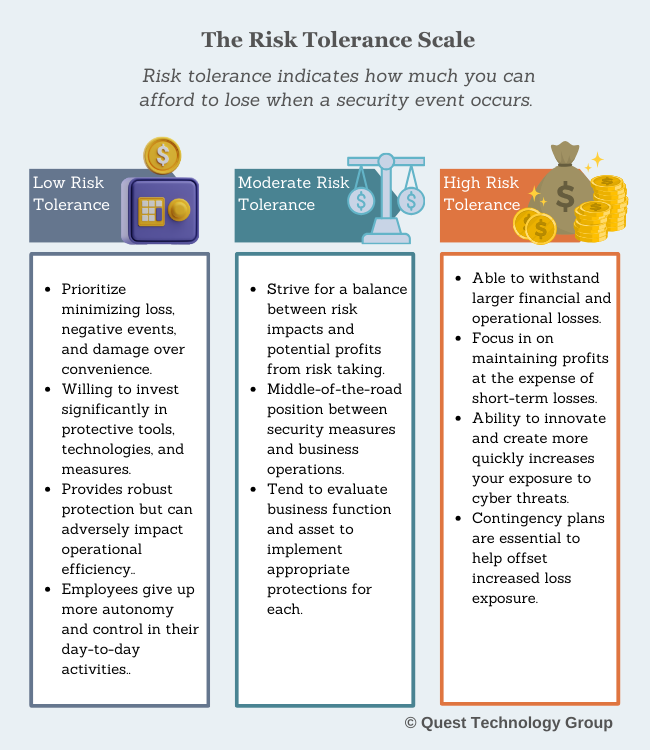
Question 1: How much can you afford to lose when a security event happens?
This is your risk tolerance and focuses on the occurrence of negative events.
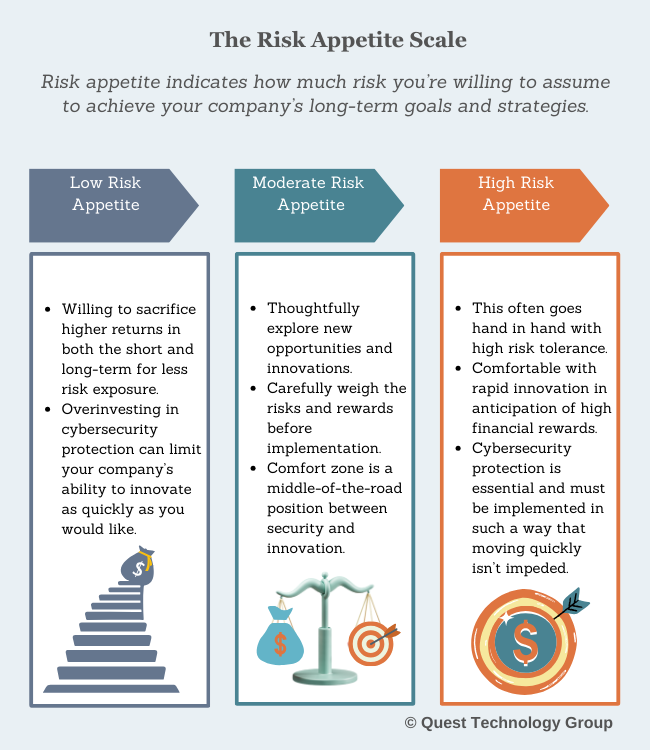
Question 2: How much risk are you willing to assume to achieve your long-term goals and strategies?
This is your risk appetite and anticipates positive outcomes.
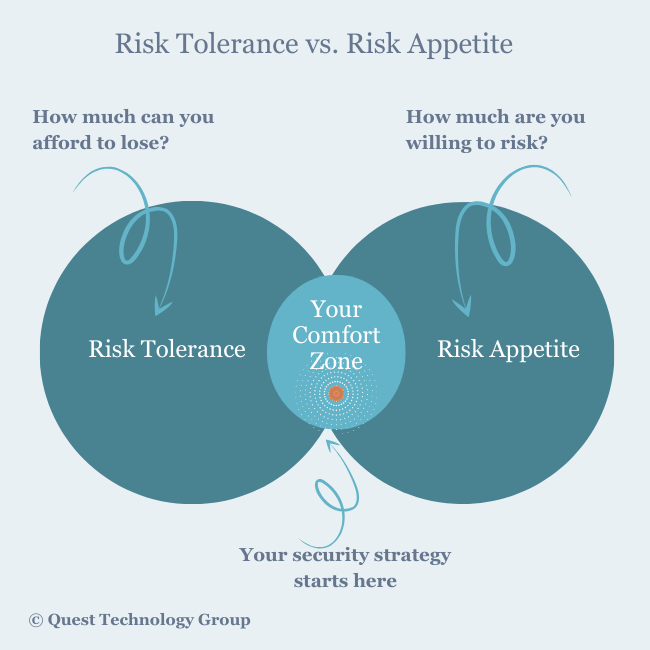
Question 3: Where is your risk comfort zone between risk tolerance and risk appetite?
This is the foundation for the security protection tailored for your company. There is no right and wrong place to land. You just need to start where you’re confident and comfortable.
While this sounds simple, there is a lot more to uncover before adopting the right security posture for your company. Every operational function in your company such as finance, operations, HR, IT, customer engagement, etc. – no matter your company size -- will have its own risk measures. Your security program must be granular and flexible.
Start with Your Free Online Cybersecurity Risk Assessments
When you're ready to explore your cybersecurity risk tolerance and risk appetite, give these two short online assessments a try. Each has 20 multiple choice questions designed to guide the cybersecurity protection decisions that are right for your company.
Cybersecurity isn't a one-size-fits-all solution so using your unique risk posture is the practical approach to your responsible security strategy. There are no right and wrong answers. The score is intended to give you a reference point for your next steps.
After you've completed your short assessments, you'll receive your free copy of After the Risk Assessments-Next Steps. This ebook will help you decode your scores and thoughtfully organize and prioritize your next action steps.
Your Risk Appetite Assessment
Your Risk Tolerance Assessment
Discover Practical Knowledge Sharing for Business & Technology Leaders
If you've ever searched for a place to connect with business leaders without the ads, sales pitches, and usual social media clutter, you know how hard that can be.

That's why we created Studio CXO. We're business leaders like you who know there can be a better way.
Explore Studio CXO Now
Free Online Cybersecurity Risk Appetite Assessment
Start with these 20 no-wrong-answer questions to guide your cybersecurity planning.

Then get your free ebook After the Risk Assessment Next Steps
Free Online Cybersecurity Risk Tolerance Assessment
Discovering how much risk you're comfortable taking is smart strategic thinking.

Then receive your free ebook After the Risk Assessment Next Steps
Tags: Cybersecurity
 Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable client relationships. She is fueled by discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner.
Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable client relationships. She is fueled by discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner. Linda believes that lasting value and trust are created through continuously listening, sharing knowledge freely, and delivering more than their clients even know they need. As the CIO of their first startup client said, "The value that Quest brings to Cotton States is far greater than the software they develop."
