How to Protect Your Backups from Malware: Infographic

Let's start with a quiz -- and don't groan. It will be worth sacrificing a minute for this one.
Question:
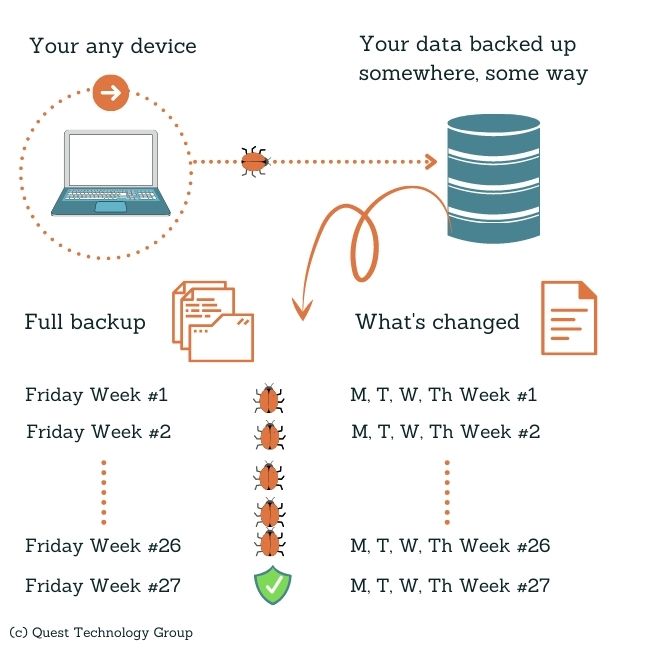
Part 1: If you do a full backup (that means every file you have) every Friday
Part 2: and incremental backups (just the files that have changed) every Monday-Thursday,
Part 3: and on average (it's often even longer) malware is undetected on a device for at least 6 months,
Part 4: how many full backups do you need to keep before you can safely restore from a malware-free backup?
Why am I asking you this question? Because we hear far too often, "I'm not worried. We'll just restore from backup if we're hacked."
Answer:
There are 4.345 weeks in an average month so you will need 27 full backups before you can restore.
Undetected infected files are backed up right along with every other file. You see where this is going.
It's unlikely that you have 27 full backups unless you are a very large company or are required by regulation to maintain a huge backup archive. Many companies keep just one or two months of full backups and their associated incrementals.
How will you know which backup is safe to use? Backups aren't flagged as infected. They all look the same. Your antivirus didn't catch the malware in the first place so it probably won't find it when you restore either.
Are you willing to lose 6 months' of valuable data?
If you are relying on legacy antivirus software such as Windows Defender or an entry level solution, it's time to move to today's advanced endpoint security. Download the quick "What's the Difference" PDF.
Review your current backup implementation with your IT provider or internal team. We won't wander down that winding road here.
Review your backup retention policy.
Test your backup recovery process regularly. It's not enough to have backups on the shelf. They need to quickly and reliably restore your company's operations every time.
Remember, backups are essential to safeguard your company's data and to restore when needed. However, they are reactive, not proactive. Backups alone aren't a substitute for an always-listening and responding security solution.
We understand this sounds tedious and boring. The reality is your business world is very different than it was just a few years ago. We strongly believe having up-to-date, complete information about boring backups is critical for your company's health.
This question is asked often. Too frequently we hear "I'm in the cloud so I don't need to worry about backups. They take care if it."
Who "they" are and what "it" is they do is a little unclear. There is simply a misguided assumption that the cloud ensures security, data protection, and a carefree work framework. While we are cloud users ourselves and appreciate the convenience it provides, we understand the underlying foundation and its risks.
We'll dive into this topic in an upcoming blog post.
If you are ready for a free, no obligation review of your security protection and backup strategy, we would love to talk with you.
Question:
Part 1: If you do a full backup (that means every file you have) every Friday
Part 2: and incremental backups (just the files that have changed) every Monday-Thursday,
Part 3: and on average (it's often even longer) malware is undetected on a device for at least 6 months,
Part 4: how many full backups do you need to keep before you can safely restore from a malware-free backup?
Why am I asking you this question? Because we hear far too often, "I'm not worried. We'll just restore from backup if we're hacked."
Answer:
There are 4.345 weeks in an average month so you will need 27 full backups before you can restore.
. . .
Will This Backup Scenario Work for Your Company?
. . .
5 Things You Can Do To Ensure a More Secure Backup
We understand this sounds tedious and boring. The reality is your business world is very different than it was just a few years ago. We strongly believe having up-to-date, complete information about boring backups is critical for your company's health.
What If You're Primarily Cloud-Based?
This question is asked often. Too frequently we hear "I'm in the cloud so I don't need to worry about backups. They take care if it."
Who "they" are and what "it" is they do is a little unclear. There is simply a misguided assumption that the cloud ensures security, data protection, and a carefree work framework. While we are cloud users ourselves and appreciate the convenience it provides, we understand the underlying foundation and its risks.
We'll dive into this topic in an upcoming blog post.
If you are ready for a free, no obligation review of your security protection and backup strategy, we would love to talk with you.
. . .
Thanks for Your Tuesday Visit
You're in business to grow and deliver what your customers and clients want most from you.
You've come to the right place. We share information, knowledge, tools, and resources to help you and your business thrive.
The Essential Advanced Security Bundle for Your Company's Everyday Protection
 Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable client relationships. She is fueled by discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner.
Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable client relationships. She is fueled by discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner. Linda believes that lasting value and trust are created through continuously listening, sharing knowledge freely, and delivering more than their clients even know they need. As the CIO of their first startup client said, "The value that Quest brings to Cotton States is far greater than the software they develop."
Tags: Cybersecurity