How to Start Your Company's Cybersecurity Program: Infographic
Published by Linda Rolf on 12/6/2021 and updated 12/16/2021

Nerdy Binge Watching
I just finished watching -- for the third and final time -- Halt and Catch Fire on Netflix. If you’re unfamiliar with this AMC series, it begins in the mid 1980’s. A nerdy team pushes their imagination and technology boundaries, ultimately creating the internet tools and technologies we rely on today.
Here are just 3 of my several takeaways after spending time with these imaginary technology builders.
How We Got Here
Let’s talk about number 3 for a minute.
Each of the significant technology advances we enjoy today was adopted slowly. There was pushback, a hesitancy to uproot the comfortable way we’ve always done things. Acceptance happened in small, often subtle, steps.
When you hit pause and revisit your journey from the mid-1980’s to now, the change is pretty astounding.
Because the way you work every day has changed so gradually, you don’t always have a clear picture of your company’s overall landscape. Think about some of the most impactful technologies you’ve adopted – email, the internet, online everything. The list is much longer than these three, but I think these three are foundational.
Because the adoption of email, the internet, online everything into your company’s operations has been so gradual, you haven’t always seen the underlying, unseen risks they have created.
Doable Cybersecurity Actions
I’m talking about security.
I know -- no one wants to talk about security because the messaging is often framed in fear. It feels like an insurance sales pitch. But the risks are real, and you should be concerned. The impacts to your company, your clients, and your employees are significant.
There is a way to get past the “it might happen someday” fear messaging. Commit to an actionable company security program that’s right for you. Now you take control.
Ready to get started?
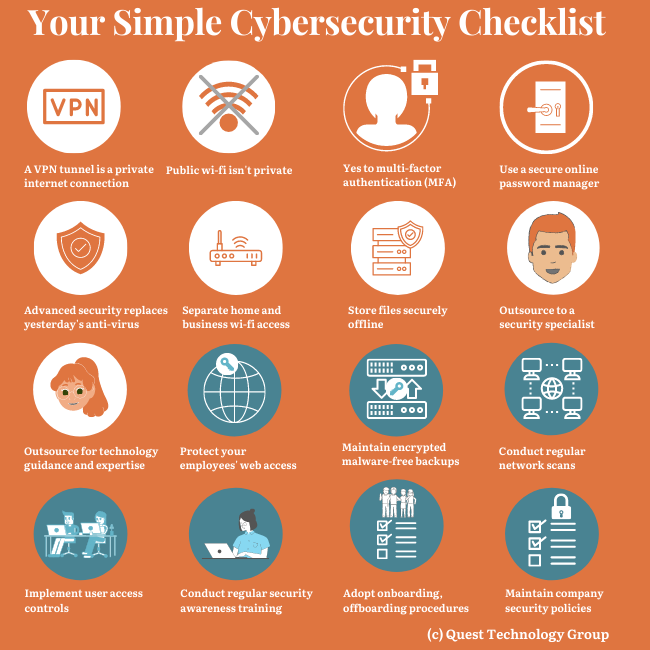
Grab More of the Checklist
. . .
 Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable client relationships.
Linda Rolf is a lifelong curious learner who believes a knowledge-first approach builds valuable client relationships. She is fueled by discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner.
Linda believes that lasting value and trust are created through continuously listening, sharing knowledge freely, and delivering more than their clients even know they need.
As the CIO of their first startup client said, "The value that Quest brings to Cotton States is far greater than the software they develop."
Tags: Cybersecurity
