Why Your Technology Team Needs Cybersecurity Skills

Cyber attacks, cybersecurity, information security, data protection, data breach. These are phrases that we are too familiar with today. In fact, they are becoming so commonplace that the temptation is to simply accept this as the new normal and move on. Have you dismissed the possibility of a breach happening in your own company?
True or False
We're not at risk for an information security breach because….
(1) We're a small company. Attackers are just interested in the big companies with a lot of data and money.
(2) We have a secure infrastructure: a firewall, anti-virus, and a backup solution.
(3) Everything is in the cloud so there are no internal security risks.
(4) Our IT team says we're secure.
(5) Our MSP takes care of all our IT needs.
(6) We have cyber insurance.
There was a time not so long ago when (1) and (2) could have been true. We are now in a very different place. The speed, sophistication, and targets of security attacks have shifted. Today more than 65% of breach attempts are focused squarely at SMBs. If your organization suffered a breach today, what would that do not only to your business but also to your valued clients?
If the immediate response is, "we'll restore from backup and continue without interruption", then consider this for a moment.
Attackers are clever. Malware can be planted and work quietly on your network for months before being discovered. You will never know that it is efficiently gathering a wealth of information about your users' activities. Imagine for a moment every keystroke that you make being captured. It happens.
Restoring from a backup has some obvious risks. What if that piece of malware was planted on your network months ago? Your successful backup has been preserving this malware for as long as it has been hiding on your network.
Your customers may have been compromised too. Capturing your activities goes beyond what your users do internally. There is a wealth of customer information that a hacker can easily exploit. Even simple email addresses are goldmines that enable phishing attacks.
Before I mislead you, we firmly believe that a well-implemented and monitored backup solution is essential. We never advise a client to overlook or minimize their backup investment. We know from firsthand experience how valuable a robust backup solution can be.
Cyber insurance is also an investment that can restore some of the financial loss. There are many factors to be considered when making a cyber insurance decision. Knowing the questions to ask your insurance provider will determine the proactive security program you must implement. Purchasing coverage does not guarantee payment in the event of a loss.
The point is that both backups and insurance are reactive. They do not prevent data breaches or attacks. They simply provide some measure of recovery or repair after an event has occurred. In both instances, the damage has been done and may not be immediately known.
Proactive monitoring, training, and continuous commitment to new security skills are the framework for today's protected organization.
This brings us to the conversation you and your IT team should have.
The conversation can feel uncomfortable, but it is the essential first step toward a more protected, informed organization. Whether outsourced to an MSP, staffed internally or a combination of these, the traditional network management and support skills alone are not enough any longer.
New cybersecurity skills need to be added to complement your existing IT team. Cybersecurity specialists do not compete with or replace your existing IT relationships.
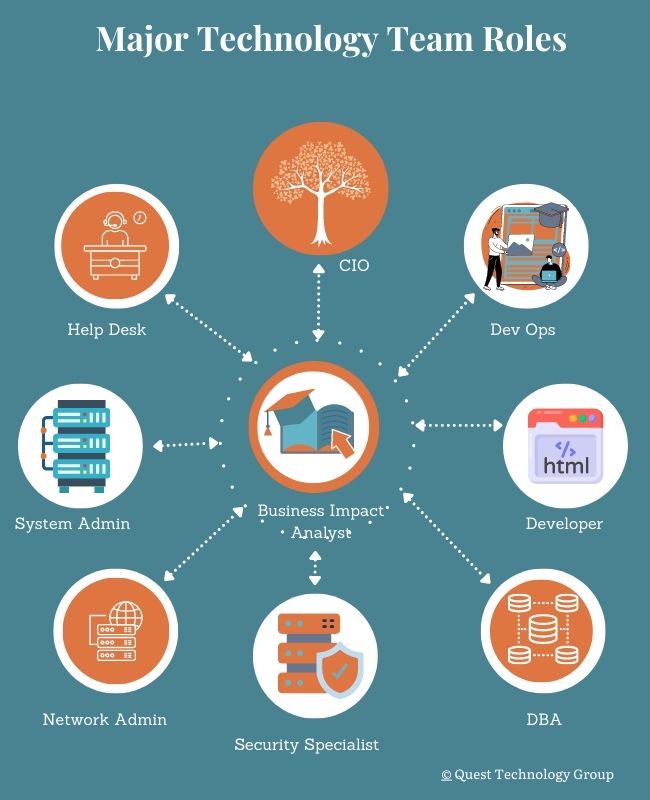
Learn more about who does what on your technology team in your free ebook offer below.
The relationship built between the IT service provider and your organization is one of mutual trust. If your IT services are provided by an outsourced MSP, it is likely that they are uncomfortable raising the subject of cybersecurity protection with you.
When you hear "IT services", it is logical to assume that everything related to IT is covered in their agreement with you. The reality is your MSP may not be providing the proactive cybersecurity services you need.
Here are just 10 of the questions to start the conversation with your MSP or internal team.
(1) What security certifications do your support team members have? While hardware and software vendor certifications are helpful in supporting the vendors' products, they are not security certifications.
(2) If we experience a cyber breach, do you cover our loss of data and legal exposure?
(3) Do you proactively monitor all of our devices for breach attempts? How do you monitor them?
(4) Are we protected and supported by a Security Operations Center (SOC)?
(5) Do you provide Dark Web monitoring?
(6) How do you monitor phishing attempts?
(7) How are all server, desktop, and laptop patches managed?
(8) What real time alerts do you receive to prevent or mitigate attacks?
(9) Do you provide risk scoring and ongoing reporting to identify security gaps?
(10) Do you provide regular security awareness training?
It's a new business landscape today. We all share the responsibility to create and maintain an informed security program in our organizations. This relies on the commitment to continuous learning, awareness, training, and staffing.
Are you ready to adopt a living security program to protect your company's most valuable assets?
What Is Your Company's Attitude Toward Cybersecurity?
True or False
We're not at risk for an information security breach because….
(1) We're a small company. Attackers are just interested in the big companies with a lot of data and money.
(2) We have a secure infrastructure: a firewall, anti-virus, and a backup solution.
(3) Everything is in the cloud so there are no internal security risks.
(4) Our IT team says we're secure.
(5) Our MSP takes care of all our IT needs.
(6) We have cyber insurance.
There was a time not so long ago when (1) and (2) could have been true. We are now in a very different place. The speed, sophistication, and targets of security attacks have shifted. Today more than 65% of breach attempts are focused squarely at SMBs. If your organization suffered a breach today, what would that do not only to your business but also to your valued clients?
If the immediate response is, "we'll restore from backup and continue without interruption", then consider this for a moment.
Attackers are clever. Malware can be planted and work quietly on your network for months before being discovered. You will never know that it is efficiently gathering a wealth of information about your users' activities. Imagine for a moment every keystroke that you make being captured. It happens.
Restoring from a backup has some obvious risks. What if that piece of malware was planted on your network months ago? Your successful backup has been preserving this malware for as long as it has been hiding on your network.
Your customers may have been compromised too. Capturing your activities goes beyond what your users do internally. There is a wealth of customer information that a hacker can easily exploit. Even simple email addresses are goldmines that enable phishing attacks.
Proactive Cybersecurity Prevention vs. Reactive Repair
Before I mislead you, we firmly believe that a well-implemented and monitored backup solution is essential. We never advise a client to overlook or minimize their backup investment. We know from firsthand experience how valuable a robust backup solution can be.
Cyber insurance is also an investment that can restore some of the financial loss. There are many factors to be considered when making a cyber insurance decision. Knowing the questions to ask your insurance provider will determine the proactive security program you must implement. Purchasing coverage does not guarantee payment in the event of a loss.
The point is that both backups and insurance are reactive. They do not prevent data breaches or attacks. They simply provide some measure of recovery or repair after an event has occurred. In both instances, the damage has been done and may not be immediately known.
Proactive monitoring, training, and continuous commitment to new security skills are the framework for today's protected organization.
The New Cybersecurity Specialist Role in Your Organization
This brings us to the conversation you and your IT team should have.
The conversation can feel uncomfortable, but it is the essential first step toward a more protected, informed organization. Whether outsourced to an MSP, staffed internally or a combination of these, the traditional network management and support skills alone are not enough any longer.
New cybersecurity skills need to be added to complement your existing IT team. Cybersecurity specialists do not compete with or replace your existing IT relationships.
Learn more about who does what on your technology team in your free ebook offer below.
The relationship built between the IT service provider and your organization is one of mutual trust. If your IT services are provided by an outsourced MSP, it is likely that they are uncomfortable raising the subject of cybersecurity protection with you.
When you hear "IT services", it is logical to assume that everything related to IT is covered in their agreement with you. The reality is your MSP may not be providing the proactive cybersecurity services you need.
Start the Cybersecurity Services Conversation with Your IT Team
Here are just 10 of the questions to start the conversation with your MSP or internal team.
(1) What security certifications do your support team members have? While hardware and software vendor certifications are helpful in supporting the vendors' products, they are not security certifications.
(2) If we experience a cyber breach, do you cover our loss of data and legal exposure?
(3) Do you proactively monitor all of our devices for breach attempts? How do you monitor them?
(4) Are we protected and supported by a Security Operations Center (SOC)?
(5) Do you provide Dark Web monitoring?
(6) How do you monitor phishing attempts?
(7) How are all server, desktop, and laptop patches managed?
(8) What real time alerts do you receive to prevent or mitigate attacks?
(9) Do you provide risk scoring and ongoing reporting to identify security gaps?
(10) Do you provide regular security awareness training?
It's a new business landscape today. We all share the responsibility to create and maintain an informed security program in our organizations. This relies on the commitment to continuous learning, awareness, training, and staffing.
Are you ready to adopt a living security program to protect your company's most valuable assets?
Thanks for Your Wednesday Visit
You're in business to grow and deliver what your customers and clients want most from you.
You've come to the right place. We share information, knowledge, tools, and resources to help you and your business thrive.
What Is Your IT Provider Doing For Your Company?
Knowing the questions to ask your IT provider or internal team is the first step in planning your company's cybersecurity protection.
This free eBook: Talking With Your IT Team About Cybersecurity gives you the questions to ask and the key listening points.
Grab Your Copy Now
. . .
 Linda Rolf is a lifelong curious learner. She is fueled by discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner. They actively contribute to each client's success through mutual collaboration, thoughtful business analysis, enterprise software development, technology integration, database design and management, opportunity discovery, business growth strategy, and marketing initiatives.
Linda Rolf is a lifelong curious learner. She is fueled by discovering the unexpected connections among technology, data, information, people and process. For more than four decades, Linda and Quest Technology Group have been their clients' trusted advisor and strategic partner. They actively contribute to each client's success through mutual collaboration, thoughtful business analysis, enterprise software development, technology integration, database design and management, opportunity discovery, business growth strategy, and marketing initiatives.They believe that lasting value and trust are created through continuously listening, sharing knowledge freely and delivering more than their clients even know they need. As the CIO of their first startup client said, "The value that Quest brings to Cotton States is far greater than the software they develop."