Understand the baffling technology words and phrases you hear every day.
The Internet
What is a Browser
What is Cache
What is a Cookie
What is Data in Transit
What is Data at Rest
What is a Data Packet
What is DNS
What is Encryption
What is End-to-End Encryption
What is HTTP/HTTPS
What is SSL/TLS
Your Company Network
What is Antivirus Software
What is DNS Content Filtering
What is Advanced Endpoint Security
What is a Firewall
What is a Modem
What is a Network
What is Remote Desktop (RDP)
Work from Anywhere
What is a Home Network
What is a Hotspot
What is a VPN
What is Wi-Fi
Life in the Cloud
What is the Cloud
Your Company Assets
What is Access Rights
What is a Data Inventory
What is Shadow IT
What is a Software Inventory
What is a Technology Roadmap
What is IT Asset Management (ITAM)
What are User Access Rights
Your Security Essentials
What is a Brute Force Attack
What is Credential Stuffing
What is an IP Blacklist
What is a Keylogger
What is Malware
What is Warshipping
What is a Whitelist
What is a Browser
What is Cache
What is a Cookie
What is Data in Transit
What is Data at Rest
What is a Data Packet
What is DNS
What is Encryption
What is End-to-End Encryption
What is HTTP/HTTPS
What is SSL/TLS
Your Company Network
What is Antivirus Software
What is DNS Content Filtering
What is Advanced Endpoint Security
What is a Firewall
What is a Modem
What is a Network
What is Remote Desktop (RDP)
Work from Anywhere
What is a Home Network
What is a Hotspot
What is a VPN
What is Wi-Fi
Life in the Cloud
What is the Cloud
Your Company Assets
What is Access Rights
What is a Data Inventory
What is Shadow IT
What is a Software Inventory
What is a Technology Roadmap
What is IT Asset Management (ITAM)
What are User Access Rights
Your Security Essentials
What is a Brute Force Attack
What is Credential Stuffing
What is an IP Blacklist
What is a Keylogger
What is Malware
What is Warshipping
What is a Whitelist
What is End-to-End Encryption?
End-to-end encryption (E2EE) applies encryption to messages and files so only the sender and the intended receipient(s) can read them. End-to-end encryption occurs at the device level. This means the messages and files are encrypted before they leave the computer or device and aren't decrypted until they reach their destination.
Data stored on servers cannot be accessed by hackers or unintended recipients because they do not have the private keys to decrypt the data. The keys needed to decrypt the secure data are only stored on the sender's and recipient's devices.
How Does End-to-End Encryption Work?
Let's use an example to see how messages and files are protected throughout their journey.
In our encryption explanation, we briefly mentioned public and private keys. This key combination is how secure message and file access is managed.
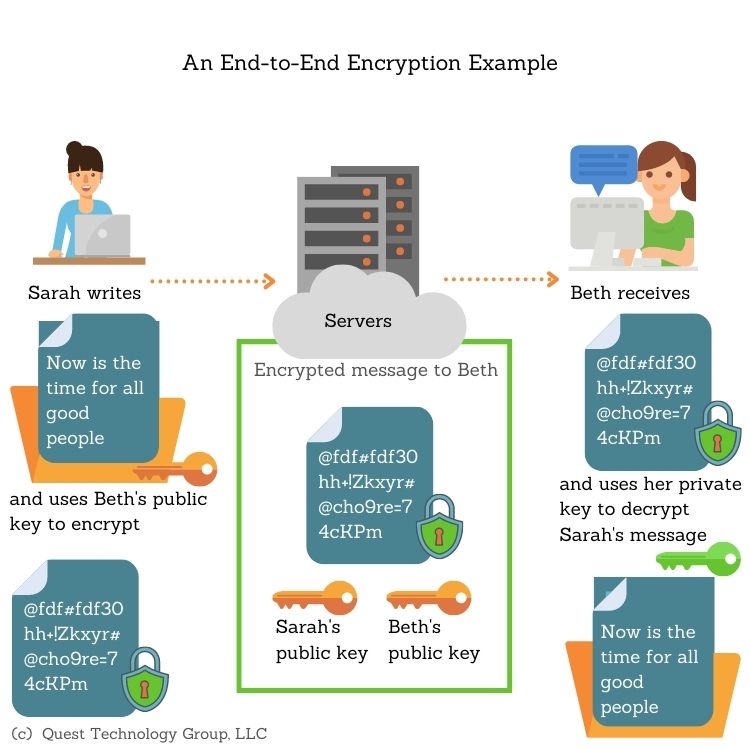
Why is End-to-End Encryption Important?
This enhanced level of encryption protects messages from sender to recipient as well as during storage. Because there is no point in sending and receiving where the data is in plaintext, the potential for hackers' access is practically eliminated.
As online meetings and learning have become the new way of doing everyday business, end-to-end encryption has become a key consideration. We'll dive into online meeting platforms and security in another topic.
We all know that data breaches have occurred, and the victims have not always been small companies. Even the most secure encryption methods and business practices cannot ensure 100% protection from hackers. However, the end-to-end encryption protection makes the hacker's job significantly more difficult.
When sharing confidential, sensitive, or personal data, end-to-end encryption is the essential standard.
Compare the example above with the plaintext to ciphertext example here. It's easy to see the benefits of end-to-end encryption.
Keep Learning
What is Data in Transit?
