Understand the baffling technology words and phrases you hear every day.
The Internet
What is a Browser
What is Cache
What is a Cookie
What is Data in Transit
What is Data at Rest
What is a Data Packet
What is DNS
What is Encryption
What is End-to-End Encryption
What is HTTP/HTTPS
What is SSL/TLS
Your Company Network
What is Antivirus Software
What is DNS Content Filtering
What is Advanced Endpoint Security
What is a Firewall
What is a Modem
What is a Network
What is Remote Desktop (RDP)
Work from Anywhere
What is a Home Network
What is a Hotspot
What is a VPN
What is Wi-Fi
Life in the Cloud
What is the Cloud
Your Company Assets
What is Access Rights
What is a Data Inventory
What is Shadow IT
What is a Software Inventory
What is a Technology Roadmap
What is IT Asset Management (ITAM)
What are User Access Rights
Your Security Essentials
What is a Brute Force Attack
What is Credential Stuffing
What is an IP Blacklist
What is a Keylogger
What is Malware
What is Warshipping
What is a Whitelist
What is a Browser
What is Cache
What is a Cookie
What is Data in Transit
What is Data at Rest
What is a Data Packet
What is DNS
What is Encryption
What is End-to-End Encryption
What is HTTP/HTTPS
What is SSL/TLS
Your Company Network
What is Antivirus Software
What is DNS Content Filtering
What is Advanced Endpoint Security
What is a Firewall
What is a Modem
What is a Network
What is Remote Desktop (RDP)
Work from Anywhere
What is a Home Network
What is a Hotspot
What is a VPN
What is Wi-Fi
Life in the Cloud
What is the Cloud
Your Company Assets
What is Access Rights
What is a Data Inventory
What is Shadow IT
What is a Software Inventory
What is a Technology Roadmap
What is IT Asset Management (ITAM)
What are User Access Rights
Your Security Essentials
What is a Brute Force Attack
What is Credential Stuffing
What is an IP Blacklist
What is a Keylogger
What is Malware
What is Warshipping
What is a Whitelist
What is User Access Rights?
Access rights are the permissions each individual user has to company applications and resources such as printers, computers, and online file storage.
Why is Managing User Access Important?
Your company has significant value not only in the data it creates and owns but also in the data your clients have entrusted to you. Employees and third party partners have the need to view, change, and delete data in their daily activities. Imagine what could happen if everyone had unlimited access to every application and its data?
How is User Access Implemented?
If you're like most company leaders, the thought of implementing a secure user access policy sounds tedious and counterproductive.
Won't controlling what employees can access just get in their way? Not at all. Your well-organized user access policy will ensure each user has what he needs to do his job. What he doesn't have permissions to won't affect his activities because he doesn't need them.
Creating a first-time policy does take time, but the benefits to your company's health and security are substantial. Once you have the policy created, a regular periodic review will ensure your company's valuable assets remain protected.
Let's walk through a basic example of role-based access control (RBAC), a widely-used method.
1 Company Users
2 Group Users by Roles
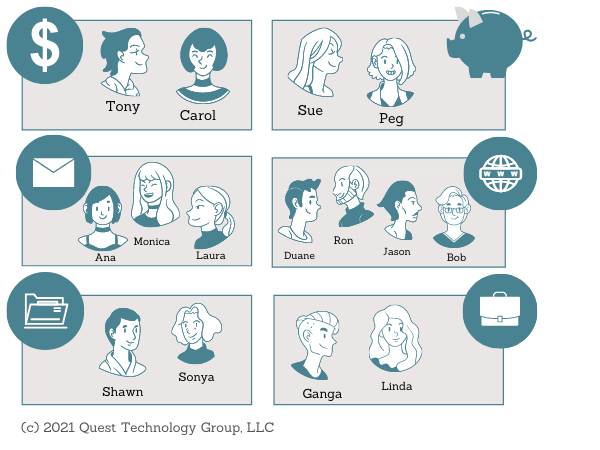
3 Their Workflow
Users have the access they need to productively and securing complete their activities. This is called the principle of least privilege. Users have access only to the data they absolutely need.
For example ---
. . . . .
